User Interface Security assessment (uisa)
Human behavior can have a significant role in causing security breaches and attacks within organizations. Some of these behaviors occur when employees or users interact with organizational applications, often due to misunderstandings or mistakes that create security vulnerabilities. While there are various ways to assess the usability of interfaces and evaluate the security risks and vulnerabilities of software, there are limited approaches that combine both aspects. To address this gap, we introduce the User Interface Security Assessment (UISA) method. This method enables application designers and developers to evaluate and quantify the security risks arising from user interactions with an application interface.
Motivation
Our method was motivated from our own experiences and research results in usable security. While designers may be well trained in methods for considering and improving the user experience, they are rarely experienced in considering the security implications of those design choices. On the other hand, security engineers are likely to overlook the impact of human behavior within an application, and have unrealistic expectations as to what users are able or willing to do. Software developers may not be familiar with either usability or security engineering, or know how to consider both of those issues together. Thus, our aim is to provide sufficient assistance based on these varied backgrounds to help a variety of stakeholders in assessing the security implications of a design, as well as provide a way to structure conversations between stakeholders with different concerns regarding usability and security.
the Handbook

The User Interface Security Assessment (UISA) guidelines involve a five-step process. The UISA handbook has been created to assist in organizing the assessment and offering direction to assessors with varying levels of expertise in UI/UX design or security. You can access and view the handbook by clicking the link provided below.
The metric
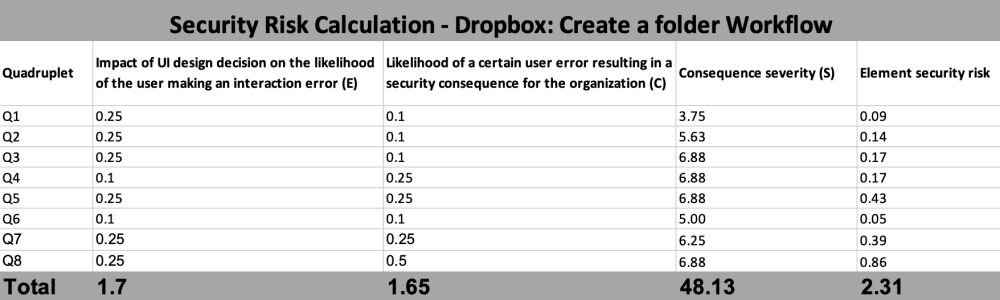
Building on the UISA method, we have also developed a metric that quantifies the security risks of the interface designs of application workflows. This metric allows stakeholders to prioritize aspects of a design that may require improvement and facilitates comparisons or tracking of different design ideas based on their potential security impact. Furthermore, we developed a metric tool that evaluators can employ to apply the metric. While the method, along with the metric, can be applied to any type of application, our primary focus is on enterprise applications used by employees within organizations. These applications have a profound influence on both organizational and customer security.
User Study
We aim to assess the effectiveness of the proposed metric by conducting multiple case studies involving design experts from various enterprise organizations. The participants will apply the metric, using the metric tool, to real applications and provide valuable feedback. The objectives of this study are:
- Determine how well the metric performs in real-world scenarios.
- Identify the strengths and weaknesses of the metric based on the participants’ feedback.
- Gather insights and perspectives from experts representing various enterprise organizations to gain a holistic understanding of the security metric’s impact.
Participation:
Participants will be asked to apply the method and the metric on a system of their own, but none of the interview questions will request participants to disclose proprietary information. However, if the participants inadvertently mention any proprietary details during the interview or focus group session, it will be redacted or anonymized during transcription before analysis. On the other hand, participating in this study might give the participants insights into the security risks of the workflows they are working on. All participants will also be given permission to keep using the method and the metric tool if they wish to do so.
The study is divided into three parts, which will take up to 2 hours in total. During the first part, a research team member will train the participants on how to use the method. In the second part, the participants will be asked to work as a group (if several participants work on the same system within an organization) or individually (if only one participant works on a certain system) to use the proposed method and apply the metric on their own software system. In the third part, a research team member will conduct an interview (if it’s only one participant working on a system), or a focus group (if it’s multiple participants working on the same system) in order to get more feedback from the participants regarding the use and the impact of the method.
Eligibility criteria:
- All participants must be at least 18 years of age.
- Participants must work on the software development, design, or the information security team within an organization.
If you are interested in participating in the user study and meet the eligibility criteria listed above, please read and sign the consent form by clicking here. The entire study is expected to take about 2 hours and participants who complete all the 3 sessions will receive a $100 Amazon gift card as a compensation for their time and cooperation. If you have any further questions regarding the method, metric, or study, please feel free to contact us at hhazazi@charlotte.edu.